When it comes to securing communication pathways and data while keeping them private, the best option, other than keeping them offline, is encryption. Cryptographic systems are systems in which data is encrypted in ways that only allows it to be accessed by authorized individuals.
This post will be focusing on symmetric and asymmetric encryption. Along with the differences, similarities, and weaknesses between the two.
Symmetric Encryption
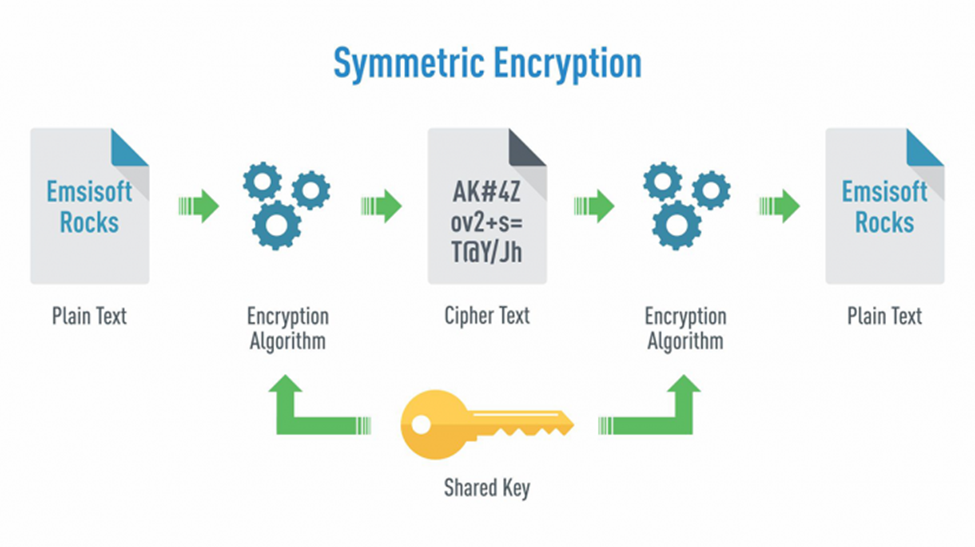
In symmetric encryption, the same key is used in both the encrypting and decrypting processes. This type is commonly used in securing communication channels and private messages. Its most prominent application has been encrypting communication between government officials for the past couple of decades.
Asymmetric Encryption
Asymmetric encryption – more commonly known as public-key encryption – uses two keys instead of one in the encryption and decryption processes. In this type of encryption, only one of the keys is public and can be shared freely without a worry, while the other needs to remain private. If one key was used to encrypt the data, the other is then used to decrypt it.
Encryption and Decryption Keys
The keys used in the encryption and decryption processes are a series of numbers produced by specialized encryption algorithms. Depending on the type of encryption, the keys’ length, speed, and uses vary.
Keys’ Length
The difference in length is the most noticeable difference between symmetric and asymmetric encryption. Encryption keys are measured by bits, and there’s a direct link between the length of the key and the level of security it provides.
With symmetric encryption, the key consists of a series of random numbers selected by a specialized algorithm. It consists of 128 or 256 bits, depending on the sensitivity and confidentiality of the data in question.
Asymmetric encryption, on the other hand, has a mathematical relationship between its public and private keys. However, having a direct link between the two keys is a serious security risk, especially since one of the keys is public.
To protect against possible attempts of unauthorized access, asymmetric keys are much longer than symmetric. For an asymmetric key to provide the same levels of protection as a 128 bits symmetric key, it needs to be 2048 bits long.
Speed
The widely different lengths of the keys mean that the encryption and decryption processes aren’t done at the same rate for both types of encryptions. How fast something works can play a huge role in whether an organization or an individual decides on using it. With the rise of high-speed in everything, a split second makes a great difference in decision-making.
Symmetric encryption works much faster, when compared to its asymmetric counterpart and requires less computational power. On the downside, since the same key is used to both encrypt and decrypt the data, it poses a much higher risk of unauthorized data access.
On the other hand, asymmetric encryption solves the vulnerability problem by using two highly complex keys and keeping one of the highly guarded and private. The downside is the long time it requires to encrypt and decrypt data along with its need for a high computational power because of its extremely long and complex keys.
Use
Since both systems naturally have their strong and weak points, they get used differently in varying industries.
Symmetric encryption, thanks to its high speed and low computational requirements, is more often used for bulk encryption or databases with a large number of users, like with payment applications.
Asymmetric encryption, with its two keys and high levels of security, is often used to keep communication channels secure. One of the most common examples is its use in encrypting emails, where the public key is used to encrypt the message and the private key, with the recipient, is used to decrypt it.
Hybrid Cryptosystems
In order to get the best of both systems, a hybrid of symmetric and asymmetric encryption was developed. Combining the strengths of both types and eliminating most of their downsides and risks. They have the simplicity of a public-key and the efficiency and speed of asymmetric encryption key, resulting in a cryptosystem that has the convenience and advantages of both types while eliminating the risks.
One example of a successful merge is the Security Socket Layer (SSL,) which works on establishing a safe communication channel between a user and a destination, like a web server. SSL, or an SSL certificate, is what guarantees a website’s safety when handling confidential data like credit card information and passwords.
********
Symmetric and asymmetric encryption systems still hold an important part in protecting data from being abused. As both systems have their advantages and disadvantages, they need to be used accordingly.
Cryptography and cryptosystems are rapidly evolving, consistently protecting users from any loopholes and backdoors found in older systems. But symmetric and asymmetric encryption remains the base of which future cryptosystems will grow from in the foreseeable future.




